Encryption at Rest using Customer Key Management
On this page
Serverless instances are in preview and do not support this feature at this time. To learn more, see Serverless Instance Limitations.
Atlas encrypts all cluster storage and snapshot volumes, securing all cluster data on disk: a concept known as encryption at rest.
Atlas Project Owners can configure an
additional layer of encryption on their data using their
Atlas-compatible customer key management provider with the MongoDB
encrypted storage engine.
Configuring Encryption at Rest using your Key Management incurs additional charges for the Atlas project. To learn more, see Advanced Security.
Atlas Project Owners can
use one or more of the following customer key management providers
when configuring Encryption at Rest for the Atlas project:
- Amazon Web Services Key Management Service
- Azure Key Vault
- Google Cloud Platform Key Management Service
After configuring at least one key management provider for the
Atlas project, Project Owners can
enable customer key management for each Atlas cluster for which
they require encryption. The key management provider does not have to
match the cluster cloud service provider.
Atlas cannot rotate customer-managed encryption keys. Refer to your key management provider’s documentation for guidance on key rotation. When you set customer key management in a project, Atlas creates a 90-day key rotation alert.
If your KMS provider becomes unavailable, this doesn't disable your cluster while it still runs. If you decide to restart your cluster, the lack of a KMS provider disables your cluster.
Configure Atlas with Customer Key Management
Encryption at Rest using Key Management requires valid key management provider credentials and an encryption key. To provide these details and enable Customer Key Management:
Navigate to the Advanced page for your project.
- If it is not already displayed, select the organization that contains your desired project from the Organizations menu in the navigation bar.
- If it is not already displayed, select your desired project from the Projects menu in the navigation bar.
- Click Advanced in the sidebar.
Enable Customer Key Management for an Atlas Cluster
After you Configure Atlas with Customer Key Management, you must enable customer key management for each Atlas cluster that contains data that you want to encrypt.
You must have the Project Owner role to
enable customer key management for clusters in that project.
For new clusters, toggle the Manage your own encryption keys setting to Yes when you create the cluster.
For existing clusters:
Navigate to the Database Deployments page for your project.
- If it is not already displayed, select the organization that contains your desired project from the Organizations menu in the navigation bar.
- If it is not already displayed, select your desired project from the Projects menu in the navigation bar.
- If the Database Deployments page is not already displayed, click Databases in the sidebar.
Validate your KMS Configuration
Atlas validates your KMS configuration:
- When you add or update credentials.
- Every 15 minutes.
- On-demand with the Encryption at Rest API endpoint.
Atlas shuts down all mongod and mongos processes on the next
scheduled validity check if one of the following conditions exist:
- your key management provider credentials become invalid
- someone deletes or disables your encryption key
If Atlas can't connect to your key management provider, Atlas doesn't shut down your processes.
If Atlas shuts down your clusters, the following events occur:
- Atlas sends an email to the
Project Ownerlisting all affected clusters. - The Database Deployments page reflects that Atlas disabled your clusters due to invalid Encryption at Rest settings.
You can't read or write data on disabled clusters. You can submit updates to disabled clusters, such as disk and instance size changes. Atlas processes these changes once someone restores your encryption key. Atlas continues to perform maintenance and apply security patches. Disabled clusters retain all your data, so billing continues.
While a cluster is disabled, Atlas does not stop the Virtual Machine (VM) the cluster is running on. Atlas may perform patches that reboot the server, but VM power is not cycled.
To regain access to your data:
- Update your credentials if they have changed since configuring Atlas with Customer Key Management.
- Restore your key if it has been disabled or deleted.
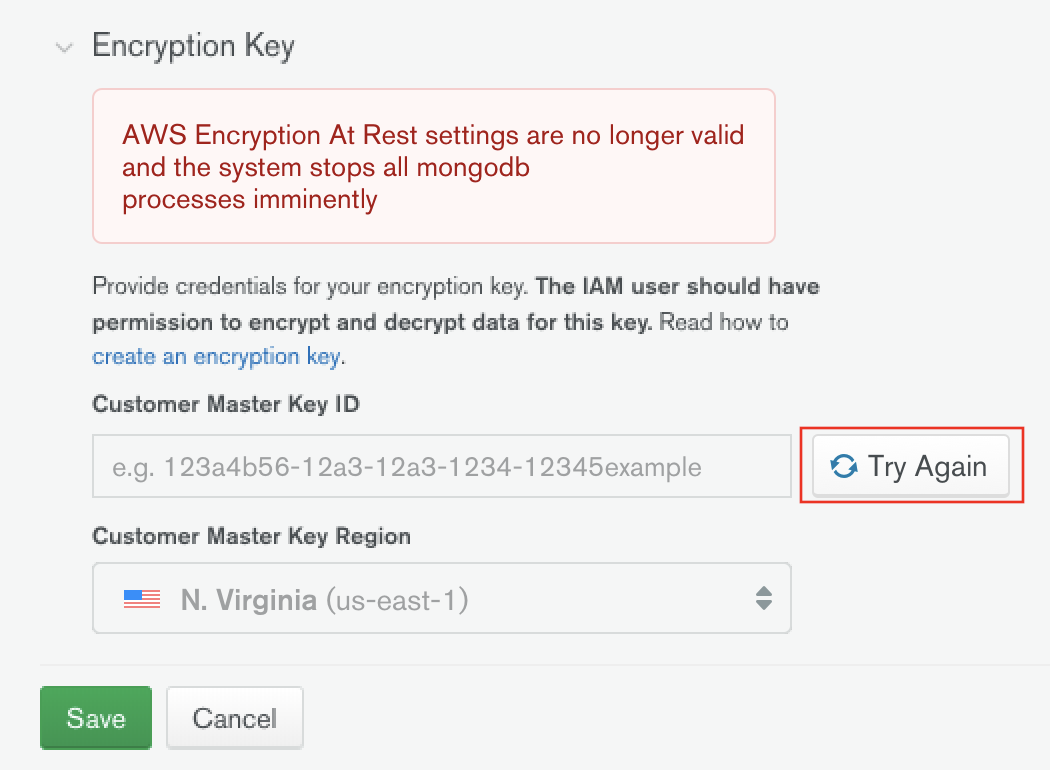
After updating your configuration, click Try Again to
validate it. If you don't, Atlas validates on its next scheduled
check. All mongod and mongos processes restart after Atlas
determines your configuration to be valid.
If your key was deleted, restore that key to regain access to your clusters. You cannot change a key or disable Encryption at Rest using Customer Key Management without a valid key.
Restore a Deleted Key
To restore a deleted key, see your key management provider's documentation:
- AWS KMS: Deleting Customer Master Keys
- Azure Key Vault: Recover Deleted Key
- GCP KMS: Destroying and restoring key versions
Encrypted Backups
Atlas encrypts all snapshot volumes. This secures your cluster data on disk. Using your cloud provider's KMS, you can:
- Encrypt your snapshot storage volumes where you store your backups.
- Encrypt the data files in your snapshots.
- Restore snapshots with the key that was active at the time the snapshot was taken.
- Encrypt PIT restore oplog data.
You cannot restore snapshots encrypted with keys that have become invalid.
You cannot enable Legacy Backups (Deprecated) on clusters encrypted with keys that you manage. You can specify a base snapshot schedule that backs up every 6 hours.
To learn more about customer key management and Cloud Backups, see Storage Engine and Cloud Backup Encryption and Restore a Snapshot of a Cluster with Encryption at Rest.